Eddy's website
Need to know something about me?
Page Menu
Latest news
October 6, 2010
HDR Defense at ENS Lyon.
Links:
CR13: Grid and Clouds
The Team
The Teaching Team:
- Eddy Caron (ENS-Lyon)
- Gilles Fedak (Inria)
- Laurent Lefevre (Inria)
- Christian Pérez (Inria)
Person in charge:
Eddy CaronGeneral Presentation
This lecture focus on a large point of view of the current distributed infrastructure. We focus on the infrastructure used in many application field: Cloud Infrastructure.
Cloud Introduction (Eddy Caron - circa 40% of the course)

In this part of the course, we plan to introduce the most important Cloud research topics. In the scope of this kind of infrastructure we will introduce Data Management (Big Data), Resources Management, Elasticity and Dynamicity, Scheduling, Budget Management, OpenStack project, etc. In other words, we will see how the science can take benefit of the Cloud.
Some references:
-
[0.1] M. Armbrust, A. Fox, R. Griffith, A. D. Joseph, R. H. Katz, A. Konwinski, G. Lee, D. A. Patterson, A. Rabkin, I. Stoica, and M. Zaharia. Above the clouds: A Berkeley view of Cloud Computing. Technical Report UCB/EECS-2009-28, EECS Department, University of California, Berkeley, Feb 2009.
-
[0.2] E. Caron, F. Desprez, A. Muresan, and F. Suter. Budget Constrained Resource Allocation for Non- Deterministic Workows on an IaaS Cloud. In 12th International Conference on Algorithms and Architectures for Parallel Processing (ICA3PP 2012), Fukuoka (Japan), September 4-7 2012. Springer.
Component Models (Christian Pérez - circa 30% of the course )

While managing the structure of an application is a difficult task for a sequential application, it is far more difficult for a distributed application. However, the mapping of the constituents of an application to resources is an important operation with respect to performance, security, or cost. This part of the module focuses mainly on component models: it will describes the concepts used by these models as well as it will present some major models used in distributed and parallel components. Last, it will introduce model transformation as an approach to deal with application structure modelization.
Some references:
- [1.1] Software Component : Beyond object oriented programming, C. Szyperski, Addison-Wesley, Reading, MA, 2002
- [1.2] Design patterns, element of Reusable Object-Oriented Software, E. Gamma, R. Helm, R. Jonhson et J. Vlissidies, Addison-Wesley, Reading, MA, 1995
- [1.3] Developing and Integrating Enterprise Components and Services, série d’articles dans “Communication of the ACM”, octobre 2002, volume 45:10
Green IT (Laurent Lefevre - circa 10% of the course)

After a survey of why energy is one of the main limitating factor for the design of large Clouds (made with DataCenters) [2.1], we will introduce the concepts of energy management and energy efficiency in Clouds [2.2]. We will focus on various clouds energy levers, models and algorithms allowing energy reduction at large scale [2.3]. Finally, we conclude by presenting on-going research done in this domain within ENS-Lyon [2.4,2.5].
Some references:
- [2.1] : Green Data Center Man : http://www.youtube.com/watch?v=VZUO5W7O7Gk - January 2008
- [2.2] : Energy-Efficient Management of Data Center Resources for Cloud Computing: A Vision, Architectural Elements, and Open Challenges , Rajkumar Buyya , Anton Beloglazov , Jemal Abawajy - 2010 - http://arxiv.org/ftp/arxiv/papers/1006/1006.0308.pdf
- [2.3] : Anne-Cécile Orgerie, Marcos Dias de Assunção and Laurent Lefèvre “A Survey on Techniques for Improving the Energy Efficiency of Large Scale Distributed Systems”, ACM Computing Surveys, to appear in 2014 - http://perso.ens-lyon.fr/laurent.lefevre/Documents/energy_acm_survey.pdf
- [2.4] : Energy Efficient Open Source Cloud Broker - 2011 - http://greencloud.ens-lyon.fr/
- [2.5] : OpenStack based Energy Efficient HPC as a Service - Jean-Patrick Gelas, Laurent Lefèvre and François Rossigneux - 2013 - http://greencloud.ens-lyon.fr/xlcloud/
Security for the Cloud (Eddy Caron - circa 10% of the course)

After a survey of different research areas of security, we will introduce the concept of system protection and especially access control. We present the current approach used to protect systems and present their shortcoming [3.1]. Then we explain how information flow can be used to enhance system protection. Based on this explanation, we present a method to provide an easy-to-use and highly secured protection mechanism for operating system [3.2]. Thereafter, we introduce the new security issues related to Cloud Computing and other virtualized Platforms [3.3]. Furthermore, we present why the protection mechanism protected before must be improved for Cloud Computing and large scale Platforms. Finally, we conclude by introducing the different hot topics on Cloud security and present on-going research done in this domain within ENS-Lyon [3.4,3.5].
Some references:
- [3.1] Michael A. Harrison, Walter L. Ruzzo, and Jeffrey D. Ullman. 1976. Protection in operating systems. Commun. ACM 19, 8 (August 1976), 461-471.
- [3.2] Patrice Clemente, Jonathan Rouzaud Cornabas, and Christian Toinard. From a Generic Framework for Expressing Integrity Properties to a Dynamic MAC Enforcement for Operating Systems. In Marina Gavrilova, C. Tan, and Edward Moreno, editors, Transactions on Computational Science XI, volume 6480 of Lecture Notes in Computer Science,
- [3.3] L. Rodero-Merino, L. M. Vaquero, E. Caron, A. Muresan, and F. Desprez. Building safe paas clouds: A survey on security in multitenant software platforms. Computer and Security, page 13, 2011. Article in press. Available online 2 November 2011.
- [3.4] Eddy Caron, Frédéric Desprez, and Jonathan Rouzaud-Cornabas. Smart resources allocation to improve cloud security. In Surya Nepal and Mukaddim Pathan, editors, Security, Privacy and Trust in Cloud Systems. Springer, 2013
- [3.5] Arnaud Lefray, Eddy Caron, Jonathan Rouzaud-Cornabas, Huaxi Yulin Zhang, Aline Bousquet, Jémy Briffaut, Christian Toinard, Security-Aware Models for Clouds, HPDC 2013
MapReduce (Gilles Fedak - circa 10% of the course)
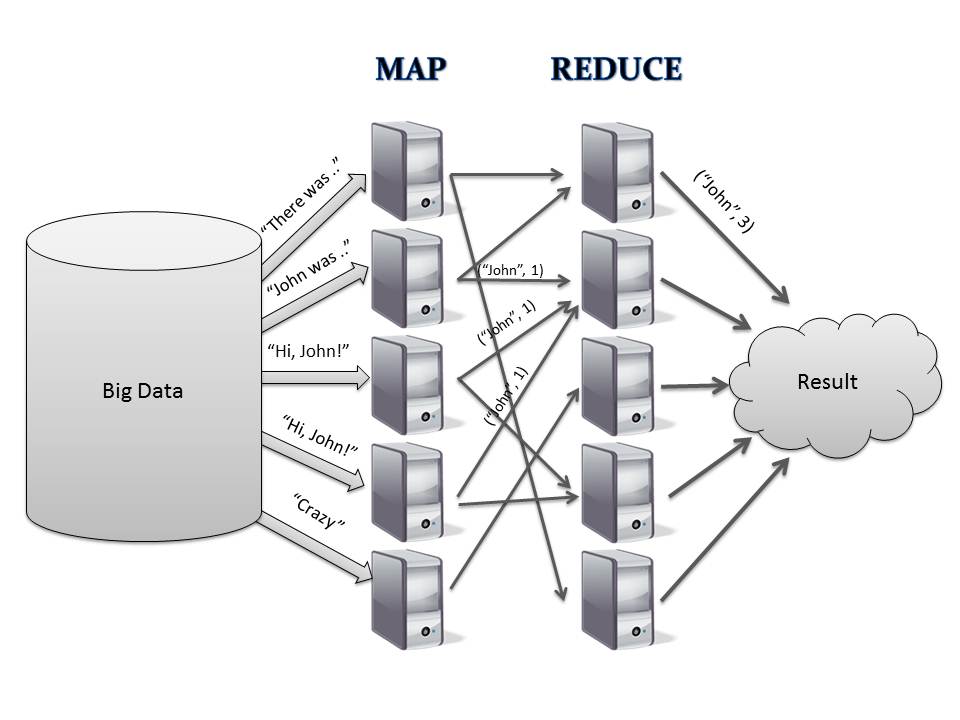
In this part we will discover MapReduce Environments: Design, Performance, Optimizations. It covers the basic design of the runtime environments, which implements the MapReduce programming model; Hadoop being the most famous one. Then, several research challenges and results are presented (task management, outliers, greener mapreduce). Finally, we introduce some of the results we obtained based on our research around MapReduce for Internet Computing.
Evaluation
Each part will be evaluated separately by either: a short homework, article reading, a short programming project, or writing a report.